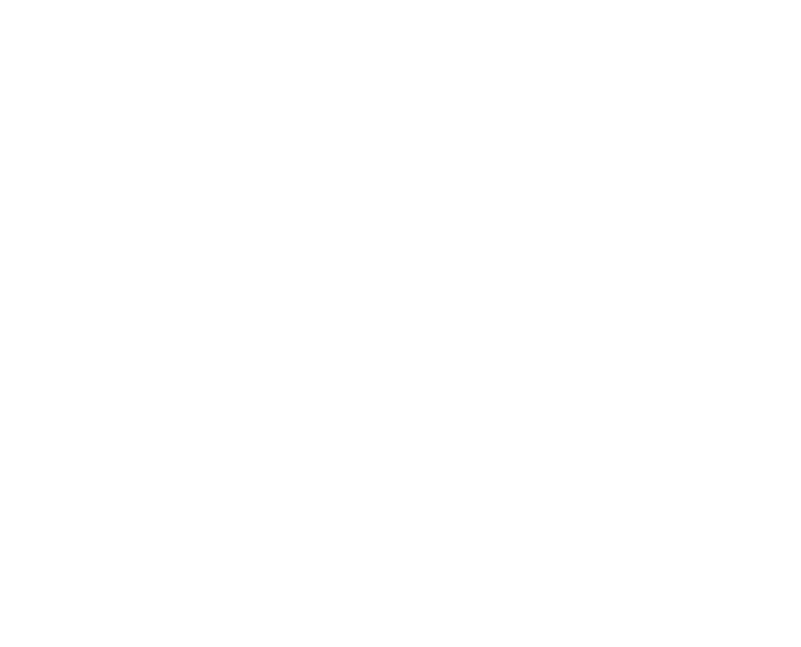Using the recent ADA breach as a backdrop, here’s a way cybercriminals could trick many of you.
I recently delivered two cybersecurity courses for dentists at the Ontario Dental Association Annual Spring Meeting.
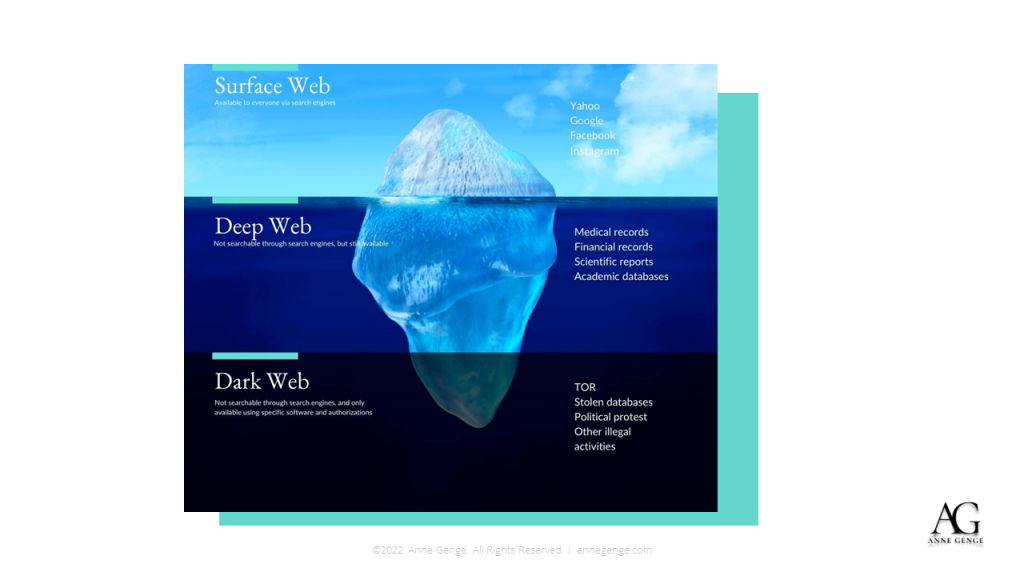
Just days before, the ADA (American Dental Association) sent out letters to members and associates that their website had been compromised. The media started reporting that sensitive data had been posted online. This gave me a perfect example to illustrate a common tactic used by cybercriminals to extricate user credentials, deliver malware, and potentially get access to many other user online accounts.
These days, ransomware commonly includes two problems for victims. The first method of attack is that data is encrypted and a ransom is requested. The second part (which has become popular in the last few years) is that data is stolen and posted on the dark web. See the diagram below which explains the difference between the different layers of the Internet and what the dark web actually is.
If I was a cybercriminal, here’s what I’d do.
I’m going to show you how a cybercriminal could leverage this breach on the ADA to trick many of the members whose data has already been posted on the dark web. (see image below to understand ‘dark web’)
I have found some information about you posted online, on the dark web. In this case I’m only going to use two pieces of information. One is that I will use the doctors name, and the second is that I will use his/her email address.
Cybercriminals are master storytellers and have spent their entire careers learning about human behavior. They know how to leverage fear, urgency, and manipulate emotion. One of the best times to strike at victims is immediately following a breach, making the attack part of the story.
Step 1: Leverage a bad situation to validate the scam
Since the cybercriminal already knows that many members have received an email (similar to the one shown in the image below), I will use the situation to create a trick that will make the person receiving the email believe that they are doing something to ensure that their account is safe.
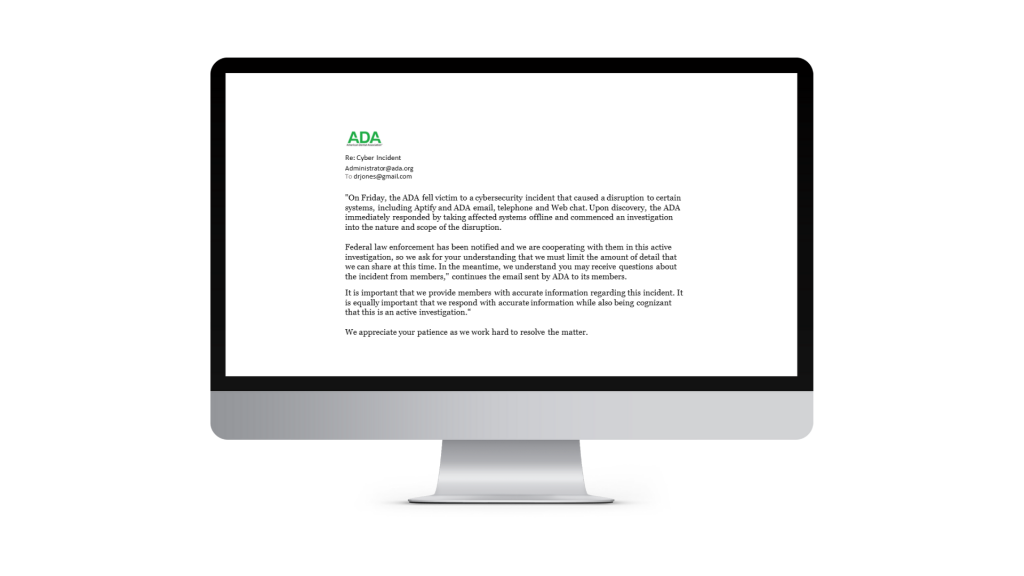
Step 2: Register a similar web domain (address)
Here’s how I will execute this attack. I will register an internet address (domain) that is very similar to the American dental Association URL. In this case I’m using “ADAmember.org”.
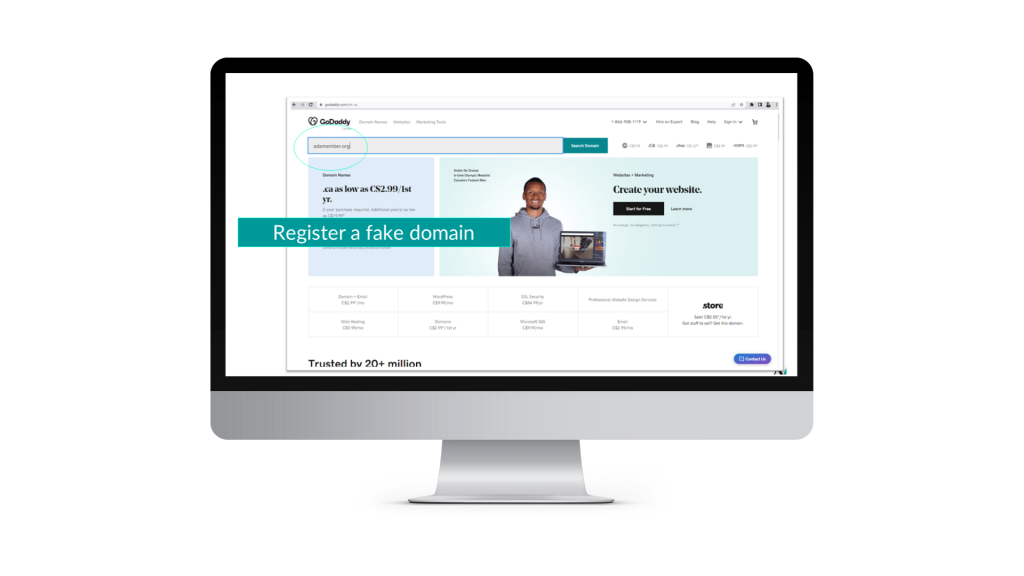
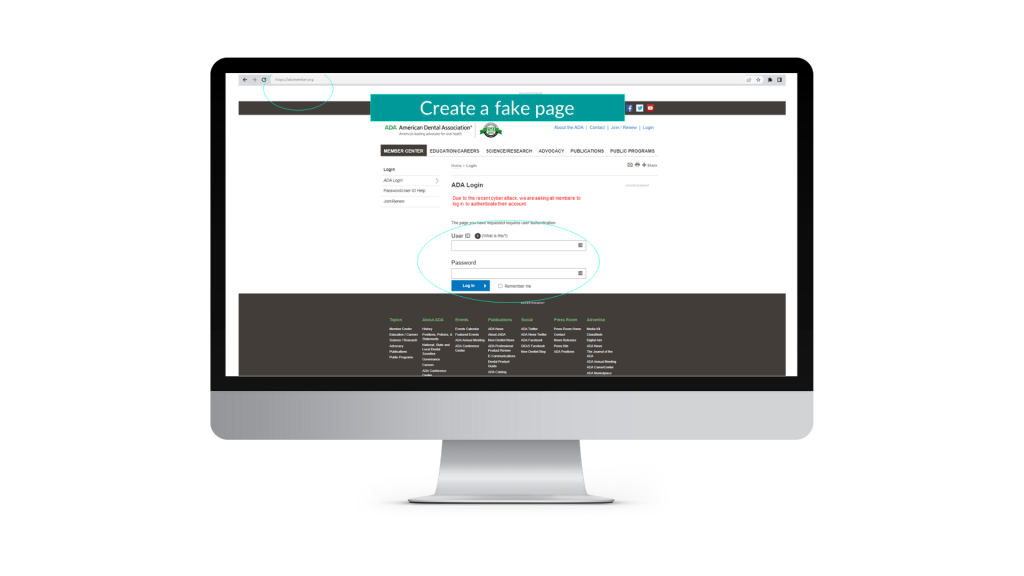
Stap 3: Create a fake but realistic copycat website
Now that I own this web address, I will create a fake login page that looks very similar, or exactly the same as the ADA member portal. I will add a little bit of information in red telling you that we need you to log in to authenticate and check your account.
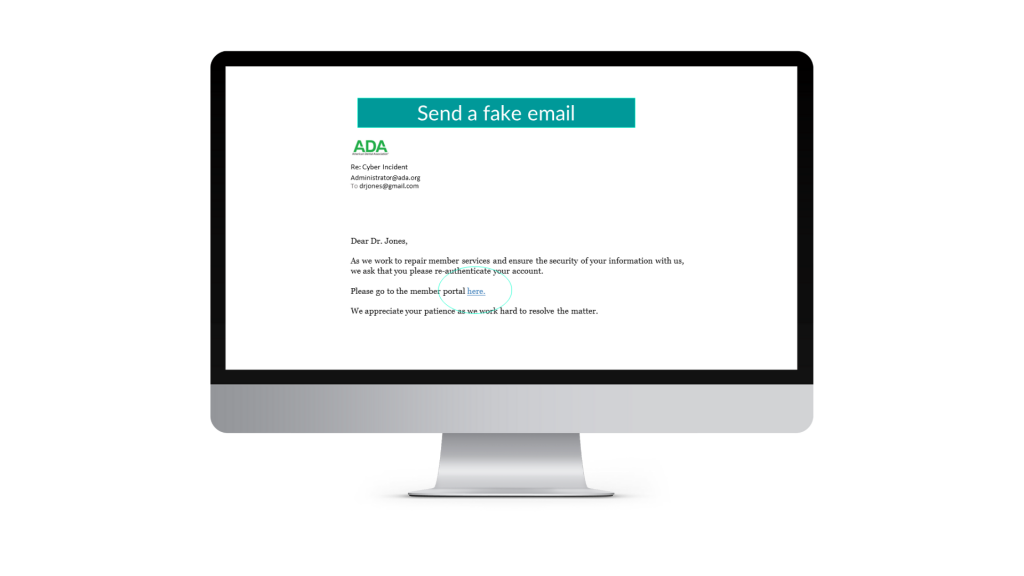
Send a phishing email to the people I found on the dark web
I will now send you an email that looks very similar to the one you received from the ADA, and I’m going to ask you to login and check your account. I will embed a link for you to log in. This will send you to the fake page I created where you are going to try to log in.
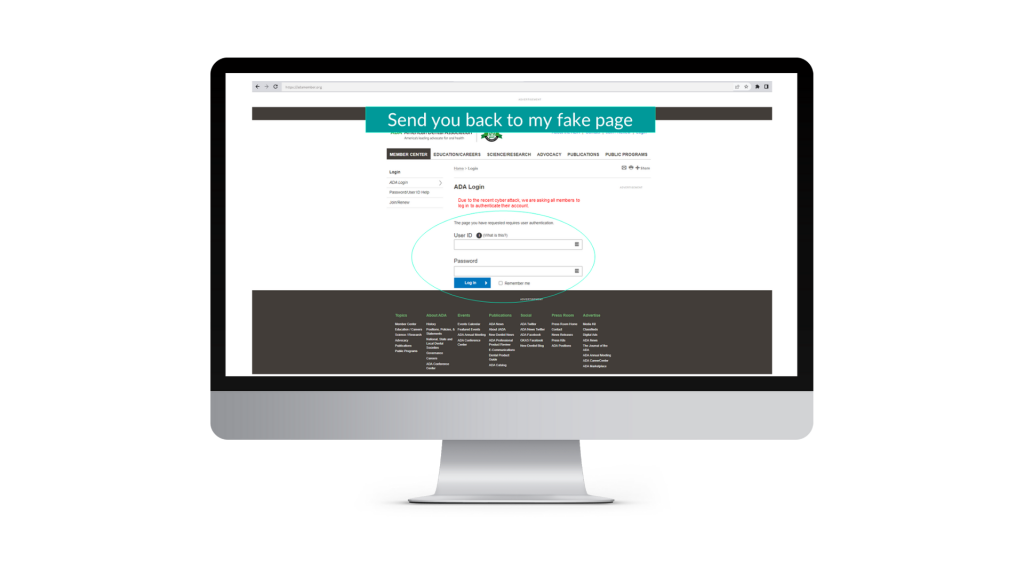
Get you to click the link to my fake login website
Here I will ask for your help. You will think you’re logging into the real ADA website, but it’s actually where I will steal your credentials.
Your login will fail. However, so as not to alarm you I will send you to another page that will explain that we need you to report that your login still does not work.
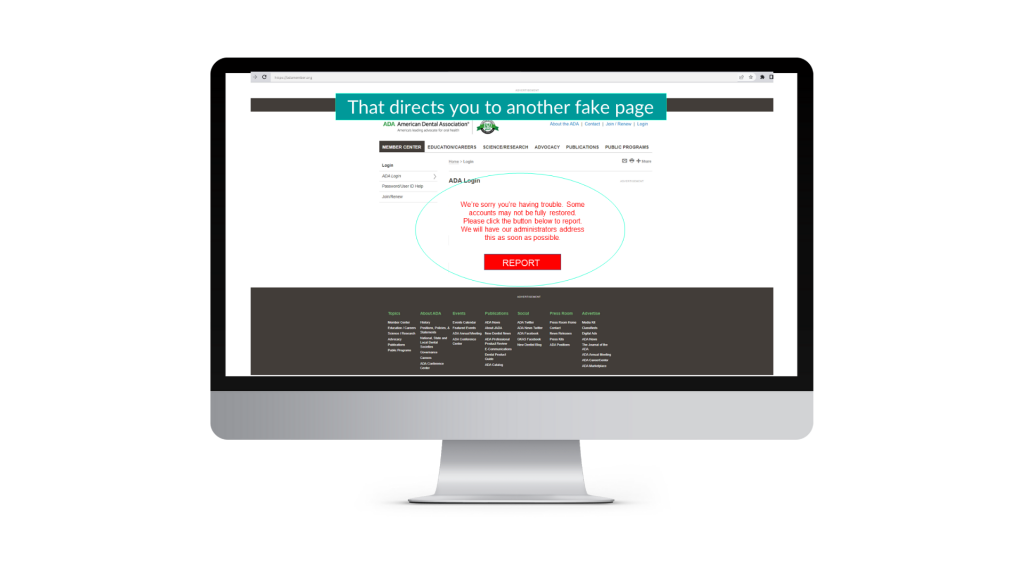
Bad guys now have your credentials and you have back door access to your systems.
This trick is likely to fool number of you, and what you won’t realize is that you will have just given me not only your login details for that ADA portal, but when you clicked the “report” button I was then able to deliver malware to your system. I could do many things with this access including:
- Spying for a while
- Stealing data
- Deploy a ransomware
- Use your PC to perpetrate attacks on others
- And more…
One Breach Can Lead To Many More
To make things worse, cybercriminals know that the login information you have used in this scenario are likely the same login credentials you’ve used across many other online accounts. Now they can check to see if they can get into any more of your accounts like your banking, your PayPal,or your social media to further my cyber crime efforts.
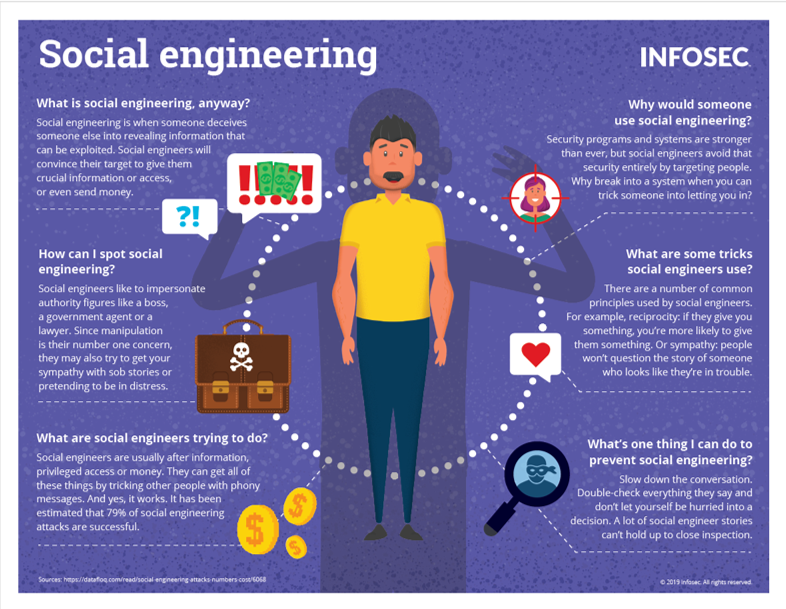
Don’t get tricked. Follow these tips.
- Carefully check URLs (web addresses) to be sure they are exactly correct. Sometimes they look identical except for a simple period, hyphen, or a space.
- Don’t follow links. Manually type in the correct URL to be sure it’s legit.
- If you know you’ve been involved in a breach, you will most certainly receive phishing emails sooner or later. Be cautious.
- Know that “buttons’ in emails or online are capable of delivering malicious files. Some do so incredibly quickly so that it’s really hard to tell. Good cybersecurity software and monitoring can catch this but if you don’t have it, you might end up with a big problem down the line.
- Use a password manager app so that you can create and store a different set of credentials for every single online account.
- Enable two-factor login wherever possible to ensure that extra layer of protection for your online accounts.
- Book a meeting with me to find out more about protecting your practice from cyber-threats.